Keysight Technologies
As the internet of things (IoT) enters into increasingly mission-critical applications, the need to guarantee the availability of service also increases. For example, a faulty or unavailable temperature sensor in a chemical manufacturing application could allow a manufacturing process violation that ruins an entire production batch, or, in the worst case, allows a pressure build-up that leads to a runaway process or explosion. An unavailable or compromised security camera could allow a criminal to commit a crime undetected. A cybersecurity hack in smart agriculture or smart logistics could disrupt a portion of the food supply or the transportation and storage network that is critical to its distribution.
This need for guaranteed availability of service is particularly true for the internet of medical things (IoMT), where absolute safety and efficacy are essential in many life-sustaining applications. This makes it uniquely susceptible to ransomware and person-of-interest attacks aimed at injuring or killing specific persons. Two areas that might disrupt the availability of service are cybersecurity vulnerabilities and premature battery failures. To address these issues, manufacturers must identify and correct vulnerabilities both inside and outside of the device.
While cybersecurity of any category of IoT devices is important (consider that the famous Mirai botnet attack used numerous consumer security cameras), the cybersecurity of devices within the internet of medical things (IoMT) is particularly important for several reasons. The most obvious reason is that many medical devices are life-sustaining devices. A failed or unavailable device could lead to painful and damaging patient outcomes, including death. The second reason is that the nature of the attack surface in the IoMT is unusual. The attack surface area is growing rapidly, and it is also a highly mobile attack surface for which physical security is impossible. Unlike, say, an industrial IoT application or smart city IoT application, a medical device in the IoMT can be any place in the world, and for wearable and embedded devices, a device may be wherever the patient is.
Furthermore, medical devices often connect to larger networks, especially at hospitals and other professional healthcare facilities. This interface multiplies the attack surface for both the hospital network and the devices. A compromised device could access information on the hospital network, and a cybercriminal could use a compromised network to launch attacks against medical devices that connect to it. The U.S. Food and Drug Administration (FDA) has issued guidance entitled Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions, and it’s very clear on this point: “[W]ithout adequate cybersecurity considerations across all aspects of these systems, a cybersecurity threat can compromise the safety and/or effectiveness of a device by compromising the functionality of any asset in the system. As a result, ensuring device safety and effectiveness includes adequate device cybersecurity, as well as its security as part of the larger system.” For this reason, “To fully account for cybersecurity risks in devices, the safety and security risks of each device should be assessed within the context of the larger system in which the device operates.”
Of course, a cybercriminal does not necessarily need to gain control over a device or run a successful denial-of-service (DoS) attack to disable a device. Anything that significantly shortens a battery-powered device’s battery life can effectively disable a battery-powered IoT device, and in some cases, the disruption can be enough to destroy the value or economic viability of an application. For example, suppose a medical device implanted in a patient is supposed to last for six to seven years. If several devices begin to fail in four or five years, the FDA and similar regulatory agencies in other countries could force a recall of the device. In the case of an embedded device, changing a battery or recalling a device may involve surgery on the patient, and that introduces additional risks.

PathWave BenchVue advanced battery test and emulation.
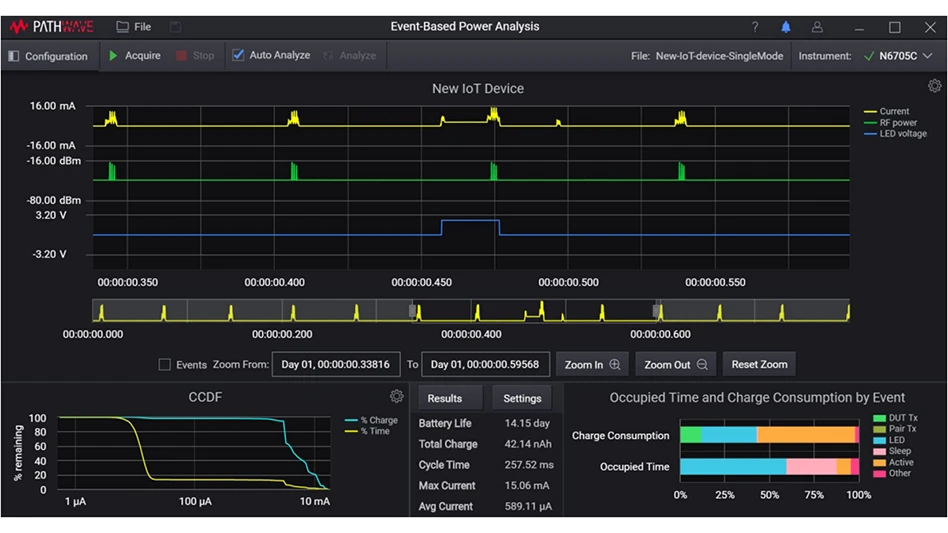
Tools such as event-based power analysis (Figure 1, above) and battery emulation using application-specific battery models (Figure 2, left) can help extend battery life, but sub-optimal hardware configurations and firmware defects can cause unexpected behaviors that limit battery life.
Fighting cybercriminals – from outside and within the device
One way to ensure the security of a mission-critical IoT or IoMT device is to use a security assessment tool that performs fully automated testing against the latest

threats and recent scenarios. Ideally, you should integrate such a tool into your continuous integration / continuous deployment (CI/CD) pipeline and ensure that you subscribe to an application and threat intelligence service to keep your cybersecurity testing up to date. While some cybersecurity tools work only at the application or device level, the best tools also work at the chipset level. For example, researchers at the Singapore University of Technology and Design used one such tool to find the notorious SweynTooth and BrakTooth families of cybersecurity vulnerabilities.
Another way to detect anomalies within devices, both intentional and unintentional, is to apply powerful machine learning tools to find unusual patterns in the device’s current waveform. IoT devices often have very predictable behaviors, and this allows you to find issues inside the device that drain the battery in unexpected ways. In the worst case, excessive current drain in an implanted medical device could heat the device to the point where it damages patient tissue. These anomalous issues could point to firmware defects, or they reveal hardware Trojans inserted into the device during the design or manufacturing processes. Either way, anomalous waveform analytics software can sift through terabytes of very precise current waveform data measured by a device current waveform analyzer to detect anomalies that can drain a battery quickly and lead to the unavailability of a device.

analytics software.
Summary
As the IoT and IoMT grow into mission-critical application areas, they become increasingly attractive targets for sophisticated attacks by cybercriminals. Device vendors must expand the way they think about cybersecurity throughout the product lifecycle. It is no longer sufficient for manufacturers to cobble together open source and homemade tools to defend against sophisticated teams of hackers. Device manufacturers must use proven, updated, integrated, and automated solutions that work inside and outside of their devices to protect their devices against cybercriminals and premature battery failure.
Latest from Today's Medical Developments
- February 2025 US cutting tool orders total $198.6 million
- The Smoothest Surfaces For Your Toughest Materials
- Extraordinary Starts Where Limits End | Okuma
- DISCOVER MORE WITH Mazak Northeast event
- Walter’s WT26 partial- and full-profile thread turning inserts
- Metalworking machinery orders increase for February 2025
- JW Winco’s practical sensor holders
- Manufacturers’ technology adoption & attitudes survey